Every day, organizations subject themselves to audit violations and data leaks when their end-users share sensitive data with third parties – essentially anyone outside of your organization. Various regulations and compliance frameworks require sensitive data to be encrypted with industry-grade security while at rest and in transit. Unfortunately, many complicated solutions make it difficult for
The main difference between Keeper and Delinea is their focus on Privileged Access Management (PAM). While both platforms offer PAM solutions, Keeper stands out as the superior choice. It provides a more comprehensive cybersecurity solution that includes password management, remote access and privileged access management, whereas Delinea only offers a PAM solution. What Is a
Updated on May 23, 2023. The main difference between Keeper and LastPass lies in their approaches to security. Keeper uses a zero-knowledge security model and encrypts data at the device and record level, while LastPass only encrypts data at the vault level making it more vulnerable to cyber attacks. Furthermore, Keeper offers a range of
Regulations and frameworks such as PCI-DSS, SOX, NIST SP 800-53, NERC CIP and HIPAA require privileged user activity to be monitored and audited sufficiently for investigation. Privileged user monitoring and auditing for databases are critical as databases often contain the most sensitive information to an organization. Many organizations leverage built-in database auditing capabilities included with
Updated on February 10, 2023. Password security is crucial to preventing cyber attacks. It is important to find a password manager that enables the zero-trust security model to mitigate the risks of data breaches from compromised user accounts. Here is a breakdown of this security framework and how Keeper helps with zero-trust compliance requirements. What
One of the selling points of cloud computing is the ability to quickly spin up new machines as needed. Unfortunately, this means that cloud environments grow very complex, very quickly – and manually updating configuration files to add new instances gets really old, really fast. It’s easy to make a mistake, which inhibits productivity and
The term “ITAR compliance” is a misnomer. Unlike FedRAMP and other compliance frameworks, there is no formal “ITAR Compliance” or “ITAR Certification” process. Organizations that fall under ITAR need to understand how the regulations apply to them and set up internal policies and controls to protect ITAR technical data. Let’s examine what ITAR is all
RSAC 2022 is happening now! RSA Conference is the world’s leading cybersecurity event offering a multitude of opportunities to learn valuable insights, network with peers, and get hands-on with cutting-edge demos. Keeper Security is proud to be exhibiting this year and will be hosting personalized demonstrations, in-depth product overview and Q&A sessions, and 1:1 meetings
Terraform is a very popular infrastructure-as-code (IAC) tool that enables DevOps teams to deploy and manage infrastructure such as servers, containers and databases. Since Keeper Secrets Manager supports record creation through Terraform, you can secure infrastructure secrets using your Keeper Vault. This feature, combined with existing credential read functionality, makes it possible to maintain your
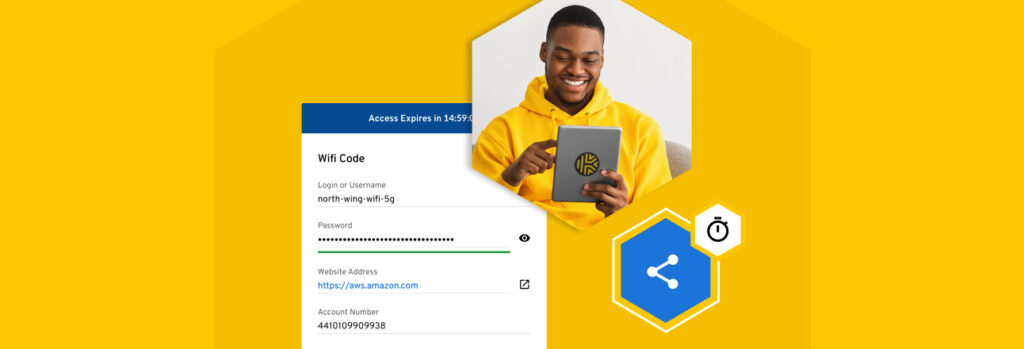
Ever need to share a password with someone, maybe a friend, a contractor or a business associate but they don’t have a Keeper account? Keeper is pleased to announce the launch of One-Time Share, a new feature that lets Keeper users securely share records with anyone on a time-limited basis, without the recipient having to
The mass migration to distributed work presented IT and DevOps teams with new challenges as they were forced to perform infrastructure monitoring and management remotely. IT and DevOps personnel needed a secure, reliable, and scalable way to remotely connect to their machines that is easy to manage. Keeper Connection Manager provides DevOps and IT teams
Cloud computing, widespread distributed work, hyper-digital supply chains, and the rapidly rising number of connected devices provide threat actors with more potential entry points into organizational networks than ever before – and they’re leveraging stolen user credentials to breach them, according to a recent Gartner blog discussing the top cybersecurity trends for 2022. It’s Not
Multi-Factor Authentication (MFA) is crucial to protecting against password-related cyber attacks. On a fact sheet the White House released earlier this week, advising organizations on how to protect themselves against potential cyber attacks in light of the crisis in Europe, the first action item is, “Mandate the use of multi-factor authentication on your systems to
Managing IT infrastructure secrets is a hassle. Ironically, deploying and maintaining most secrets management solutions is at least half the battle. Typically, installing a secrets manager requires purchasing and installing additional on-prem hardware, then enduring a complex and time-consuming software installation process, and maintaining servers moving forward. Keeper Secrets Manager (KSM) was designed to be
Keeper is pleased to release an updated version of our popular browser extension, which incorporates new productivity and user experience enhancements that our customers have been asking for. This includes a simpler, more holistic workflow when creating new records. Easily Choose Which Email Address to Use for New Records Between work, school, and our personal
Secrets management is an integral part of container security. Application code frequently depends on infrastructure secrets, such as API keys, passwords, and access tokens. Too often, developers and DevOps personnel hard-code these secrets into container images or inject them as environment variables. Both of these methods leave secrets vulnerable to compromise. Additionally, hardcoding secrets couples
With over 80% of successful data breaches being due to compromised login credentials, password managers are an essential tool for consumers. However, while cybersecurity starts with password security, it doesn’t end there. As ever-greater portions of our lives shift online, more of our data is being digitized. All of it needs to be properly secured,
Why Is Accessibility Important? According to the World Health Organization (WHO), about 15% of the world’s population has a disability. The U.S. Census Bureau estimates that 18.7% of the U.S. population has a disability with almost 30 million people having motor or vision difficulties that impact their ability to access online websites, applications, and documents.
On Dec 10, 2021, Keeper’s security team researched a publicly-reported vulnerability regarding an open-source Java logging library developed by the Apache Foundation called Log4j (vulnerability number CVE-2021-44228). Within 24 hours following the public disclosure of CVE-2021-44228, Keeper’s security and DevOps teams published updates to its infrastructure and enterprise software applications to remediate and replace all
One week after T-Mobile initially disclosed that it had been victimized by a data breach, the news just keeps getting worse for the telecom giant. What the company originally thought was a breach impacting just under 50 million consumers has now grown to over 53 million — and, as T-Mobile stresses on its website, it