Keeper Compliance Reports
Reports provide on-demand visibility of access permissions to your organization’s credentials and secrets.
Keeper Compliance Reports allow Keeper Administrators to monitor and report the access permissions of privileged accounts across the entire organization, in a zero-trust and zero-knowledge security environment
As Identity and Access Management (IAM) cybersecurity regulations increase, organizations require comprehensive policies and tools to ensure compliance. The ability to audit and control access to credentials and sensitive information is critical to obtain compliance and prevent a data breach.
Compliance regulation costs are on the rise and staffing budgets are constrained
Distributed remote work has exponentially increased the attack perimeter for cybercriminals. Auditing access control policies has become more critical than ever. Audit and finance teams require cost-effective tools which enable remote auditing, monitoring and event reporting.

Keeper Enterprise has the most comprehensive event logging and reporting tools for compliance auditors
Streamline your security compliance process
Keeper Compliance Reports supports audits for Sarbanes Oxley (SOX) and other regulations that require access-control monitoring and event auditing. On-demand compliance reports can be forwarded to automated compliance systems and external auditors.
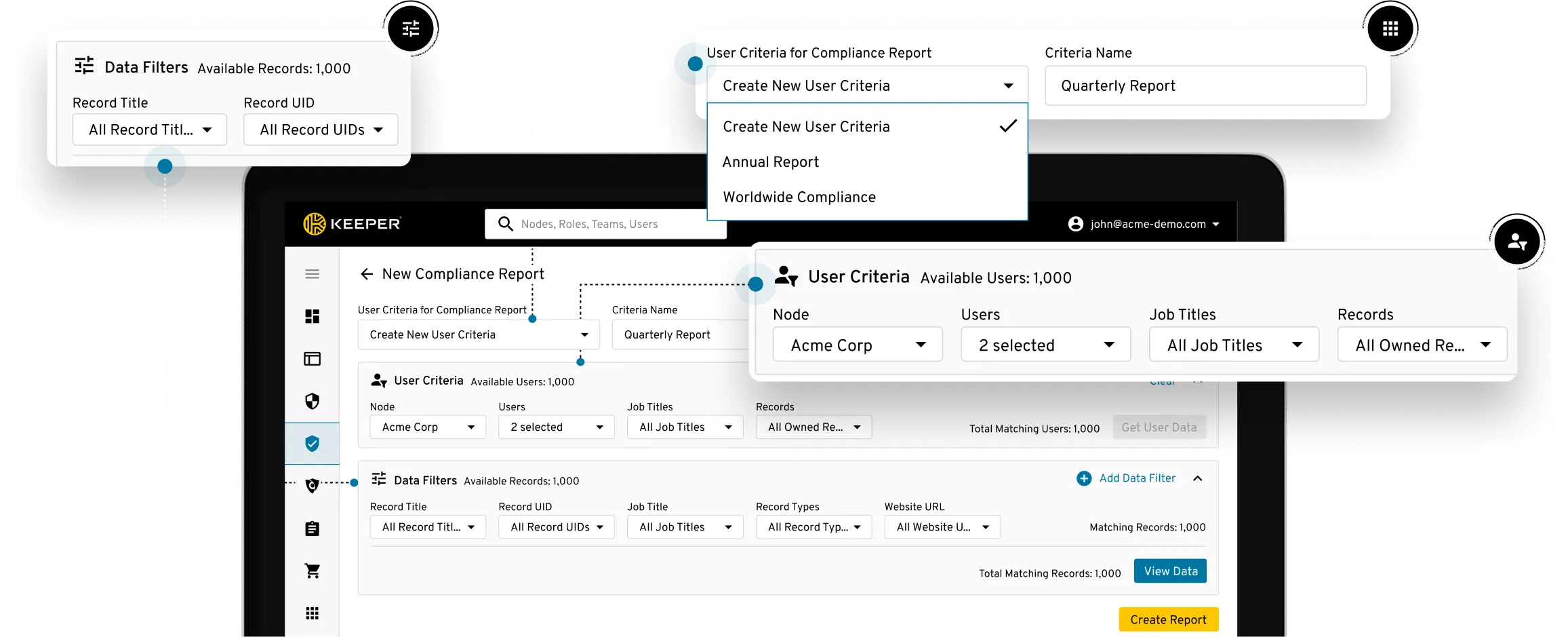
Compliance Report Capabilities
- Administrator-defined reports
- Role-based access to reports
- Report user filters with Node, User Names and Job Titles
- Record data filters with Record Titles, Record Types and URLs
- Visibility to source permissions and restrictions
- Report previews of user reports
- Report exporting to CSV, JSON and PDF
Supports critical use cases in your enterprise
On-Demand Auditing
Generate detailed, user-level reports showing privileged access and permissions to critical systems, credentials and secrets.
Payment Card Access
Analyze role-based, user-level access permissions and rights to payment card accounts.
Financial Services Investigations
Track suspicious user activity and access rights for specific financial services URLs and records to support investigations which can be utilized with Keeper’s Advanced Reporting & Alerts for comprehensive event reporting and monitoring.
Cloud Infrastructure Access Monitoring
Obtain full visibility of the organization’s cloud infrastructure (e.g. Entra ID (Azure), AWS, Google Cloud) credentials and user access permissions.
User Decommissioning
Take detailed snapshots of key elements of a user’s vault prior to decommissioning and transferring their vault to another designated user.
Specific Record-Level Searches
Quickly find records with specific attributes - e.g. record title, record type, URL, record owner(s) and job title(s).
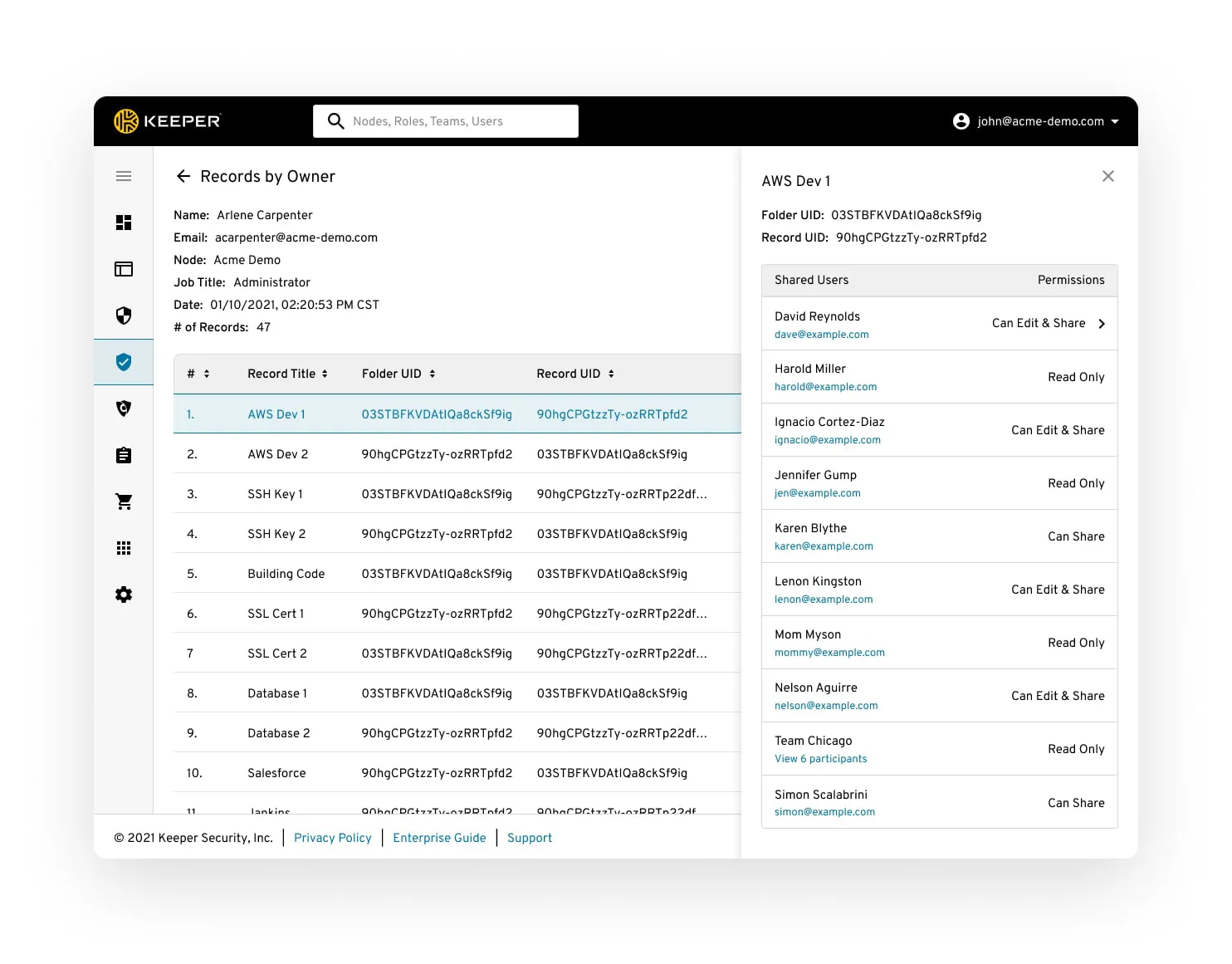
User Record Permissions Reconciliation
Provides the administrator with pervasive visibility to records that have been shared to a user through multiple sources with different permissions and restrictions.