Remote Privileged Access Management
Provide employees, vendors and trusted third parties with privileged remote access to critical systems without requiring a VPN.
Provide employees, vendors and trusted third parties with privileged remote access to critical systems without requiring a VPN.
15% of breaches involved a third party in 2023, a 68% increase from 20221
More than 35% of breaches involved credentials in 20231
IT leaders recognise compromise of privilege credentials by external threat actors2
As the number of remote and external workers increases, cyberthreats are keeping pace, bringing new and unique challenges to organisations of all sizes. One such challenge is ensuring these users can access systems and resources without adding risk or reducing productivity. This becomes an even greater issue when securing access for privileged users.
Both internal and external privileged users often require a VPN-based approach to perform remote privileged tasks. This adds complexity as it often requires additional setup on the front end for IT admins and reduces the ability for end-users to connect from anywhere and from any device, reducing productivity.
Meeting these needs while maintaining security and compliance can lead to frustrations and difficulty for IT teams, driving the adoption of Remote Privileged Access Management (RPAM).
RPAM enforces least privilege principles through session-brokering approaches and enables time-bound, session-specific, just-in-time access for remote privileged users. It also ensures accountability by recording and auditing remote privileged user activities.
RPAM is used to improve identity lifecycle management approaches, especially for short term access, which requires a specific set of policies and procedures to guide the creation and assignment of privileges and their expiration of access.
Without a proper strategy in place, securing remote privileged users can be complex.
Enable least privilege access to vendors and other outside agencies to obtain full visibility over actions with reporting and compliance built in.
Manage the entire lifecycle of privileged remote connections, ensuring least privilege and eliminating standing access.
Record privileged sessions to ensure compliance, create an audit trail of activities and mitigate threats.
Beyond internal remote users, organisations also need to secure vendors and external agencies when accessing privileged data. By extending remote privileged access to outside users, organisations benefit from a full audit trail of vendor actions and limit standing access.
Furthermore, organisations can enforce Two-Factor Authentication (2FA) and enable just-in-time provisioning to ensure only approved external users are accessing information.
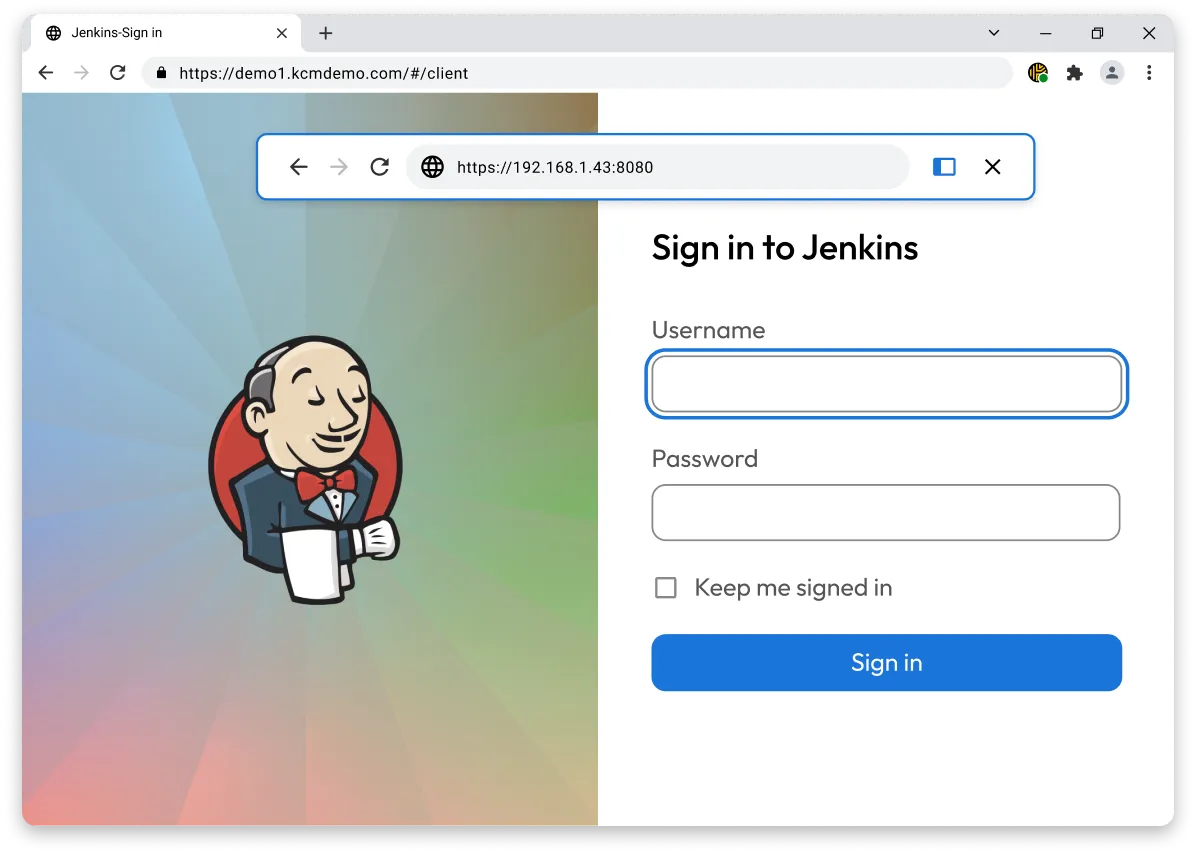
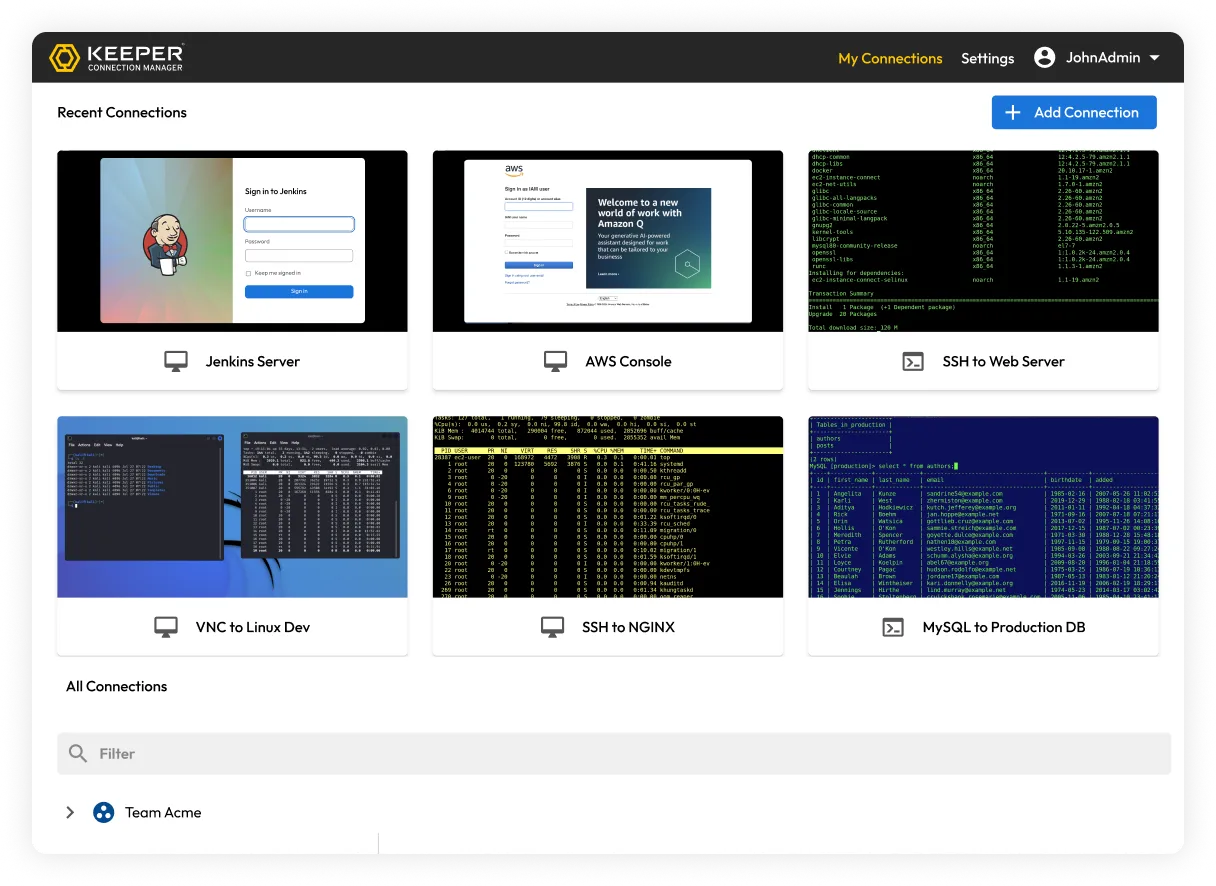
Keeper Connection Manager and Remote Browser Isolation provide session recording, credential autofill and clear audit trails to enable secure browsing and zero-trust infrastructure access without a VPN or local agent.
1 2024 Verizon DBIR Report
2 Keeper's Cloud-Based Privileged Access Management
You must accept cookies to use Live Chat.