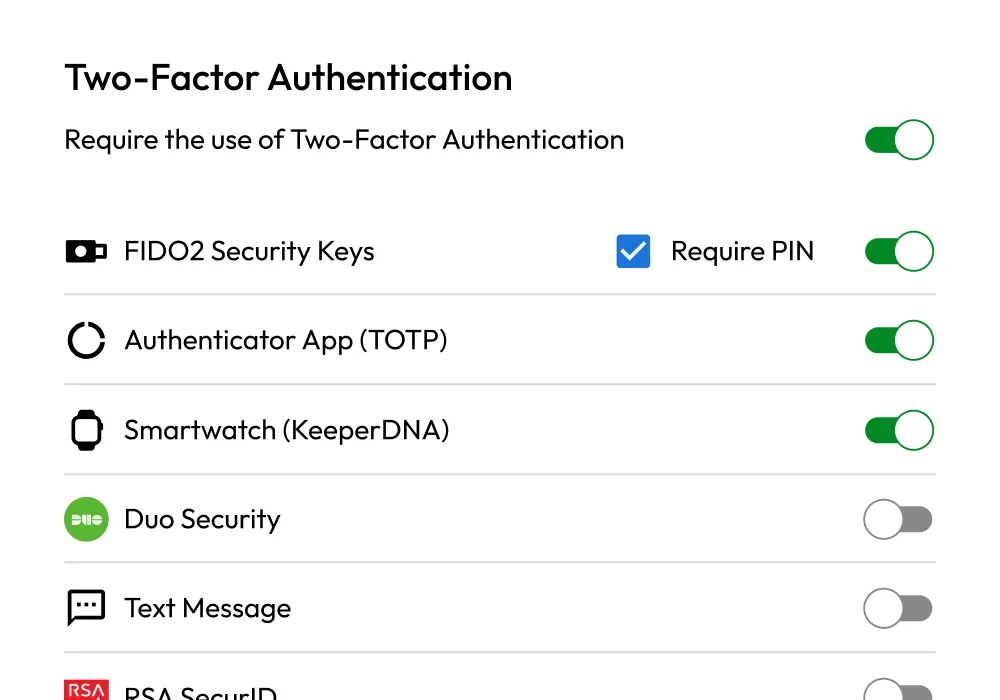
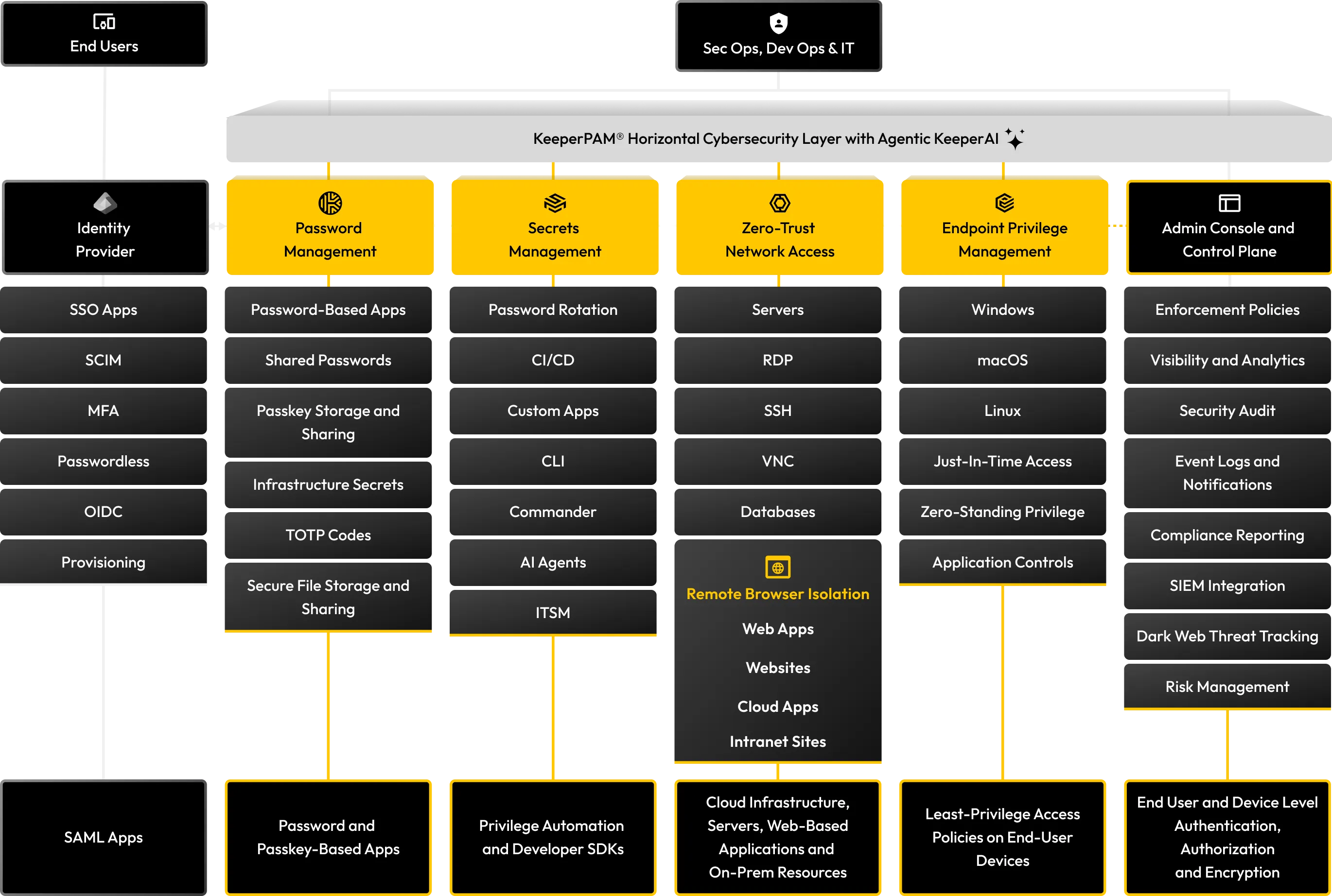
Password management
Protect and securely share passwords, passkeys and confidential data in a zero-knowledge vault with role-based access control, auditing and reporting.

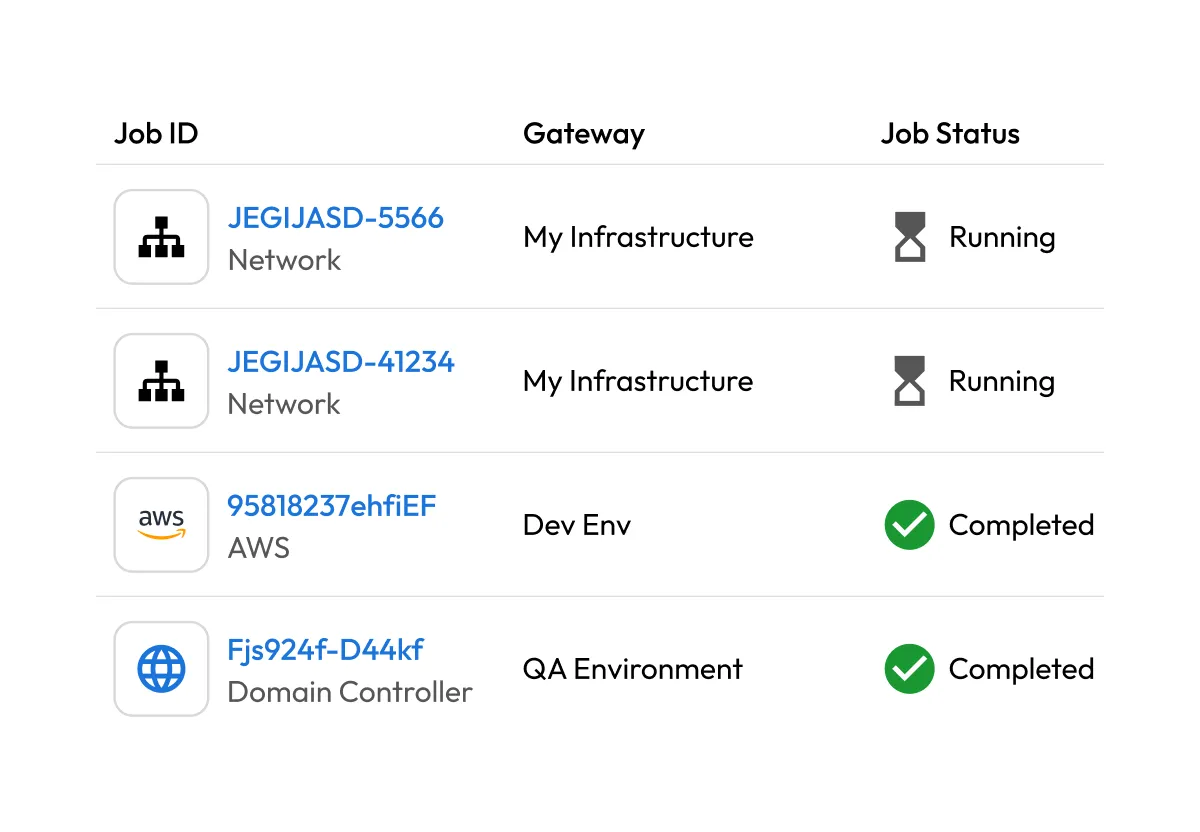
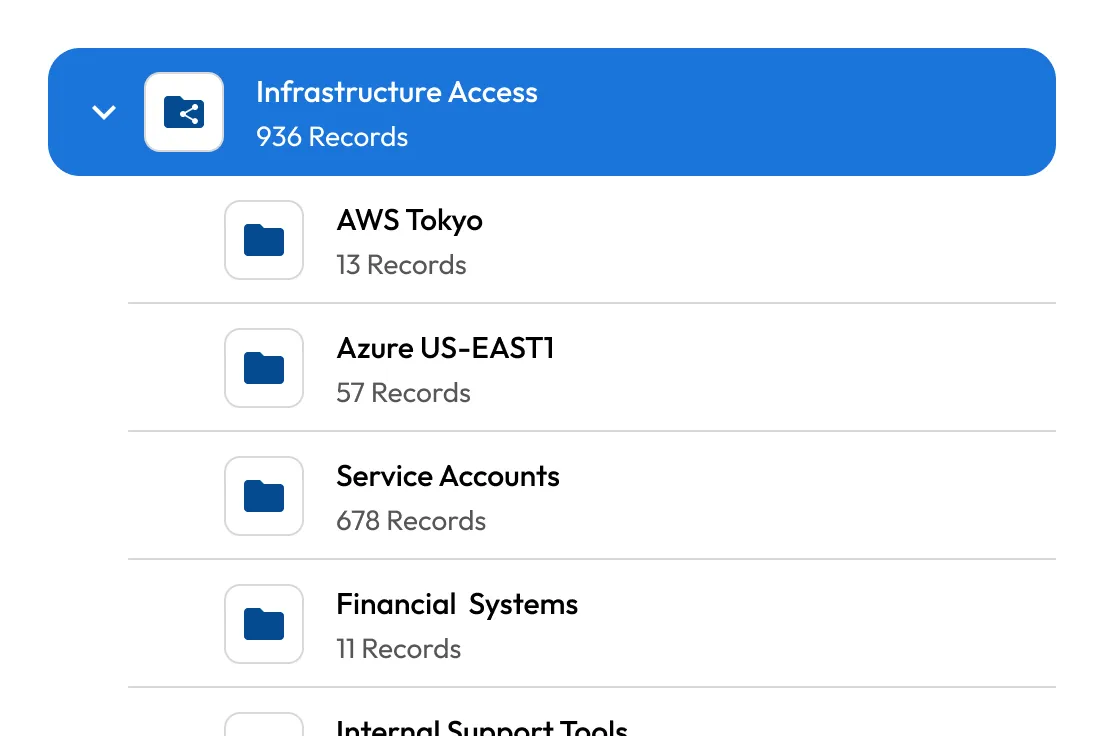
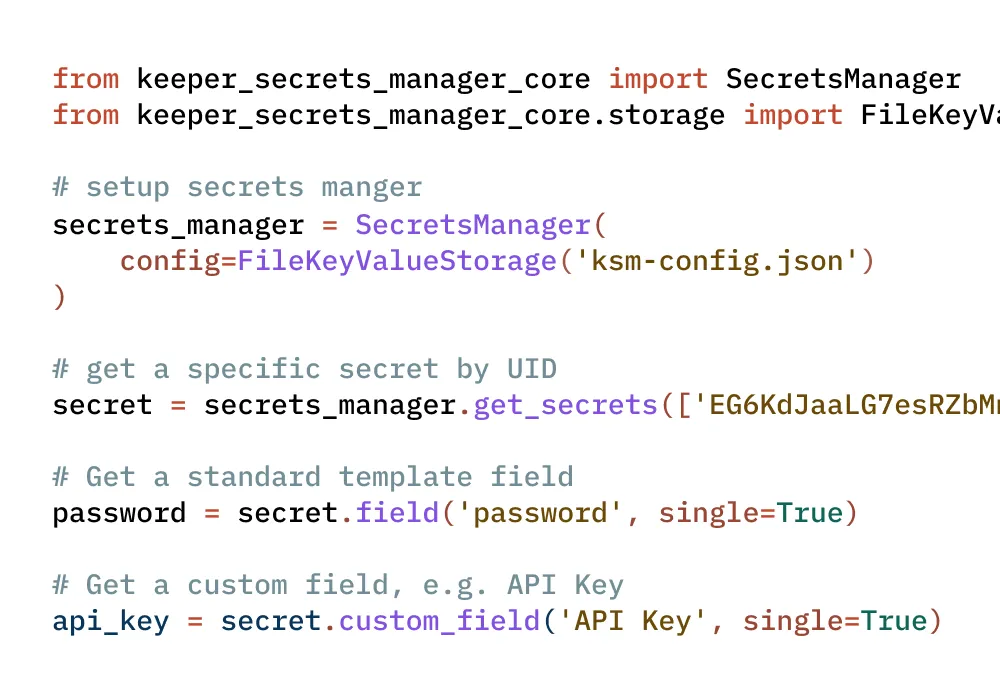
Secrets management
Integrate CI/CD pipelines, DevOps tools, custom software and multi-cloud environments into a fully-managed, zero-knowledge platform to secure infrastructure secrets and reduce secrets sprawl.

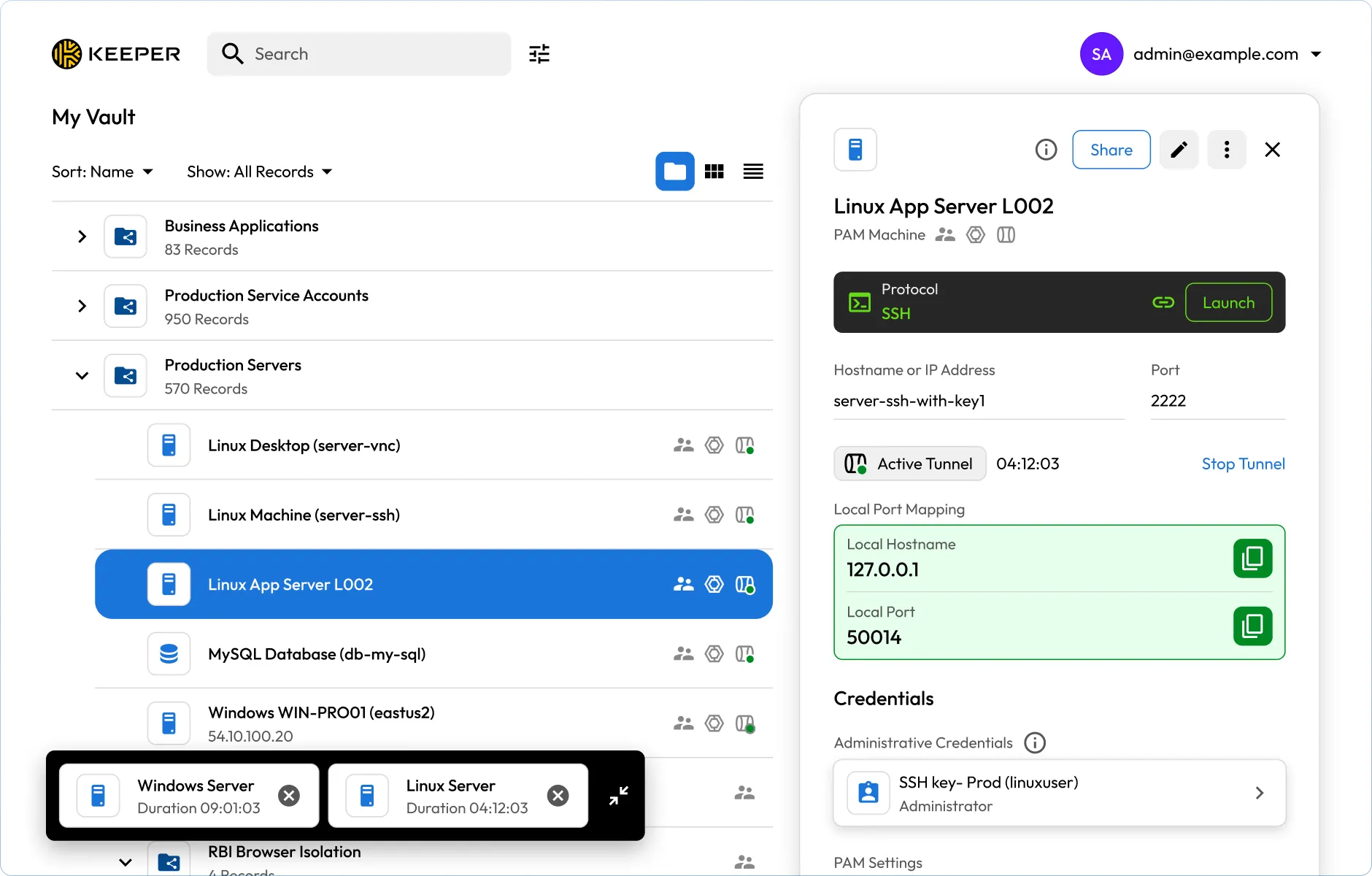
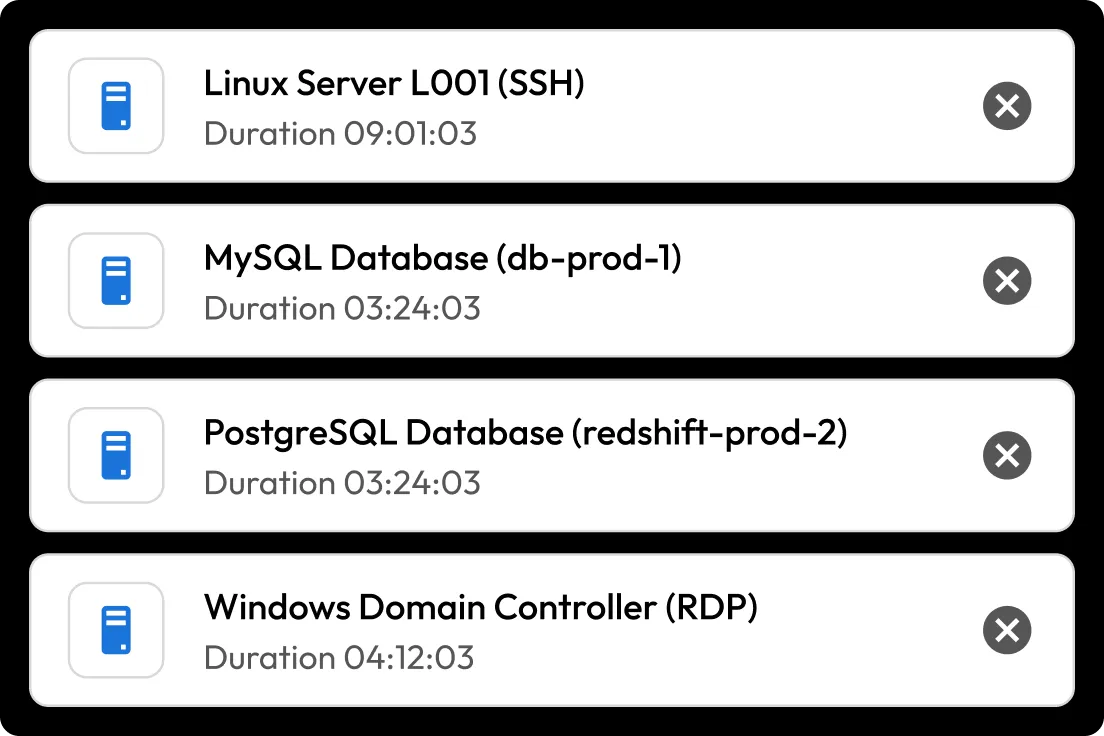
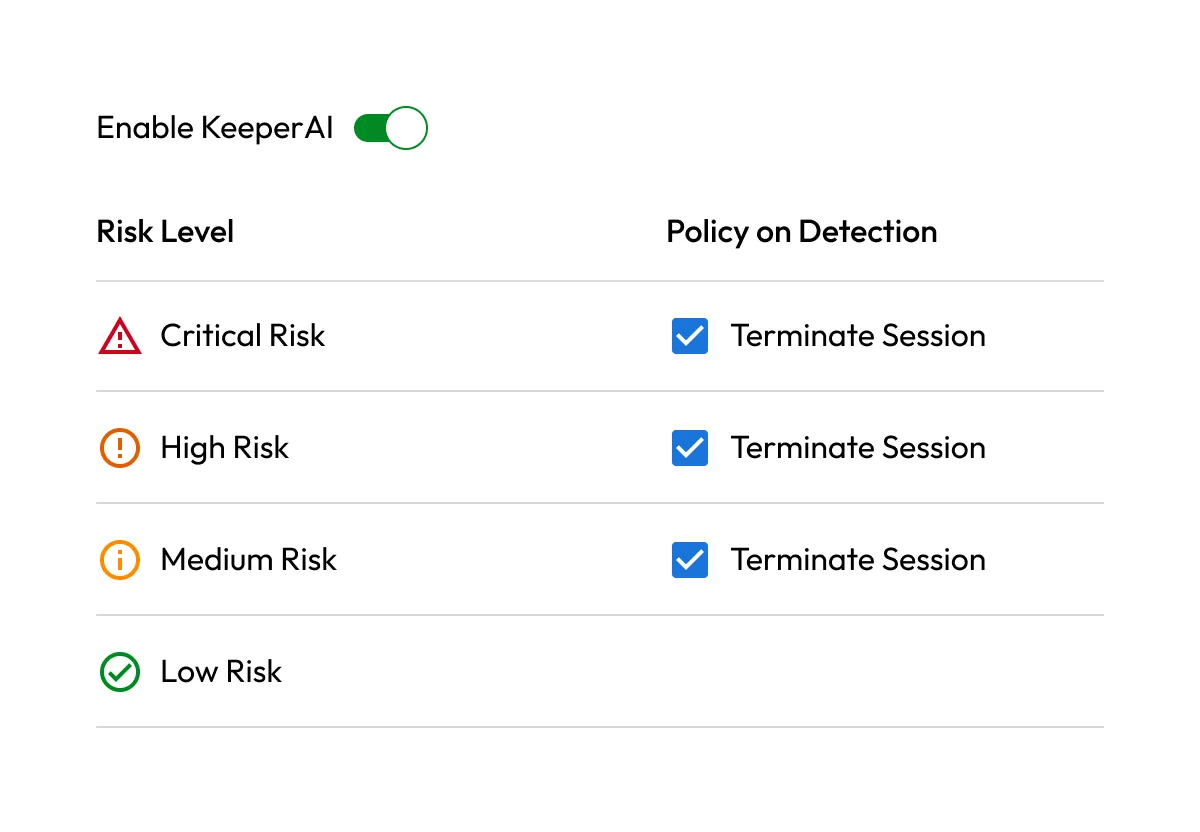
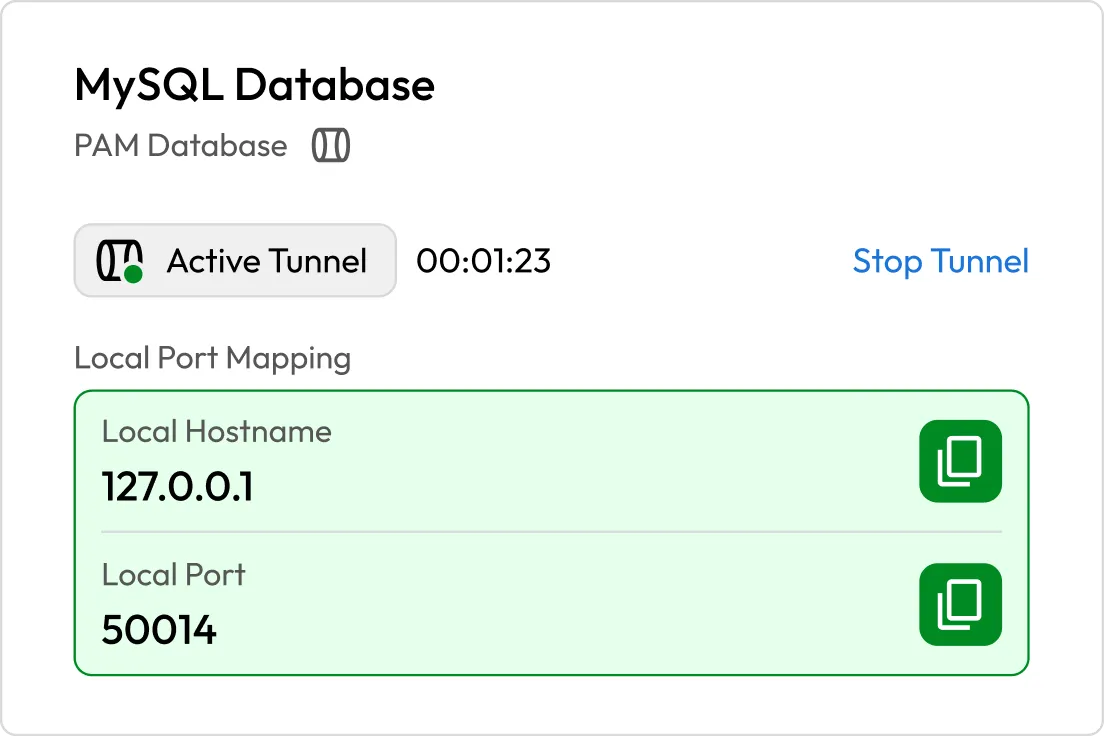
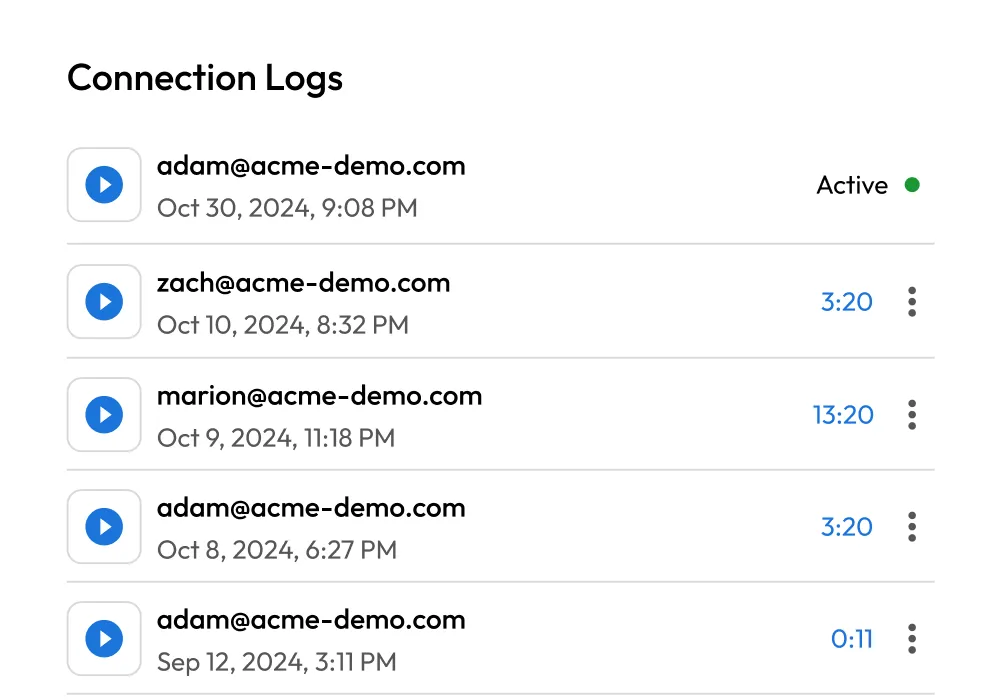
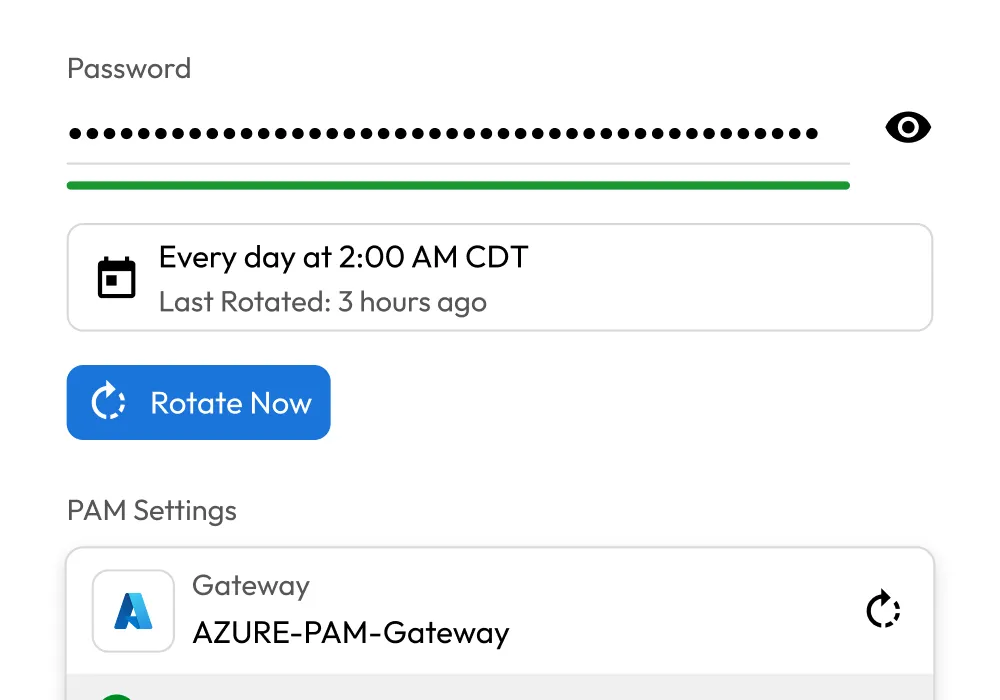
Session management
Provide secure, credential-free access to sensitive systems while maintaining full visibility and control over privileged sessions.

Remote browser isolation
Secure internal web-based applications, cloud apps and BYOD devices from malware, prevent data exfiltration and control browsing sessions with full auditing, session recording and password autofill.

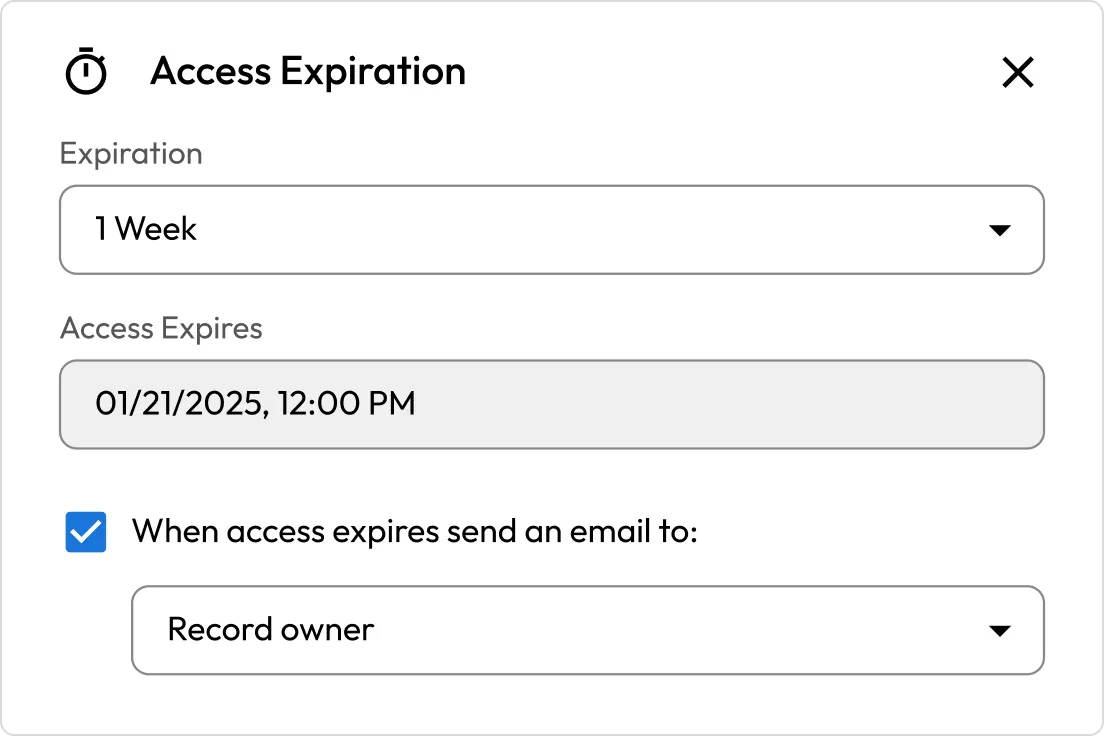
Just-in-time access
Achieve zero standing privileges and enable Just-in-Time (JIT) access across all Windows, Linux and macOS endpoints, with optional approval workflows and MFA enforcement.

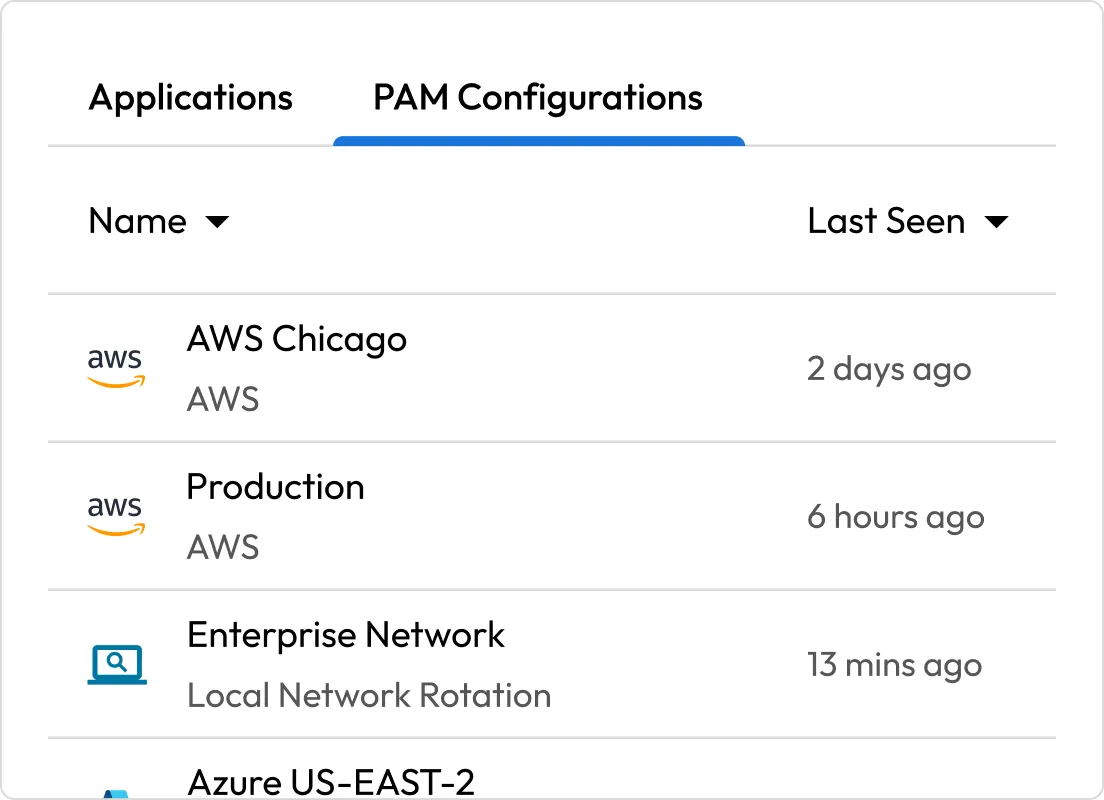
Admin console and control plane
Streamline deployment, user provisioning and policy enforcement through a centralized admin interface that seamlessly integrates with your existing identity stack.