Expedite CMMC With Keeper Security.
Keeper Security Government Cloud (KSGC) password manager and privileged access manager is FedRAMP Authorised and addresses your Cybersecurity Maturity Model Certification (CMMC) requirements.
Keeper Security Government Cloud (KSGC) password manager and privileged access manager is FedRAMP Authorised and addresses your Cybersecurity Maturity Model Certification (CMMC) requirements.



The Cybersecurity Maturity Model Certification (CMMC) is the Department of Defense (DoD) cybersecurity compliance and certification program focused on the independent assessment of defense contractors against NIST 800-171 security controls for protecting Controlled Unclassified Information (CUI).
CMMC builds upon the existing DFARS 252.204-7012 regulations. Access controls and data protection are at the forefront of the model to reduce the risk of cyber threats.
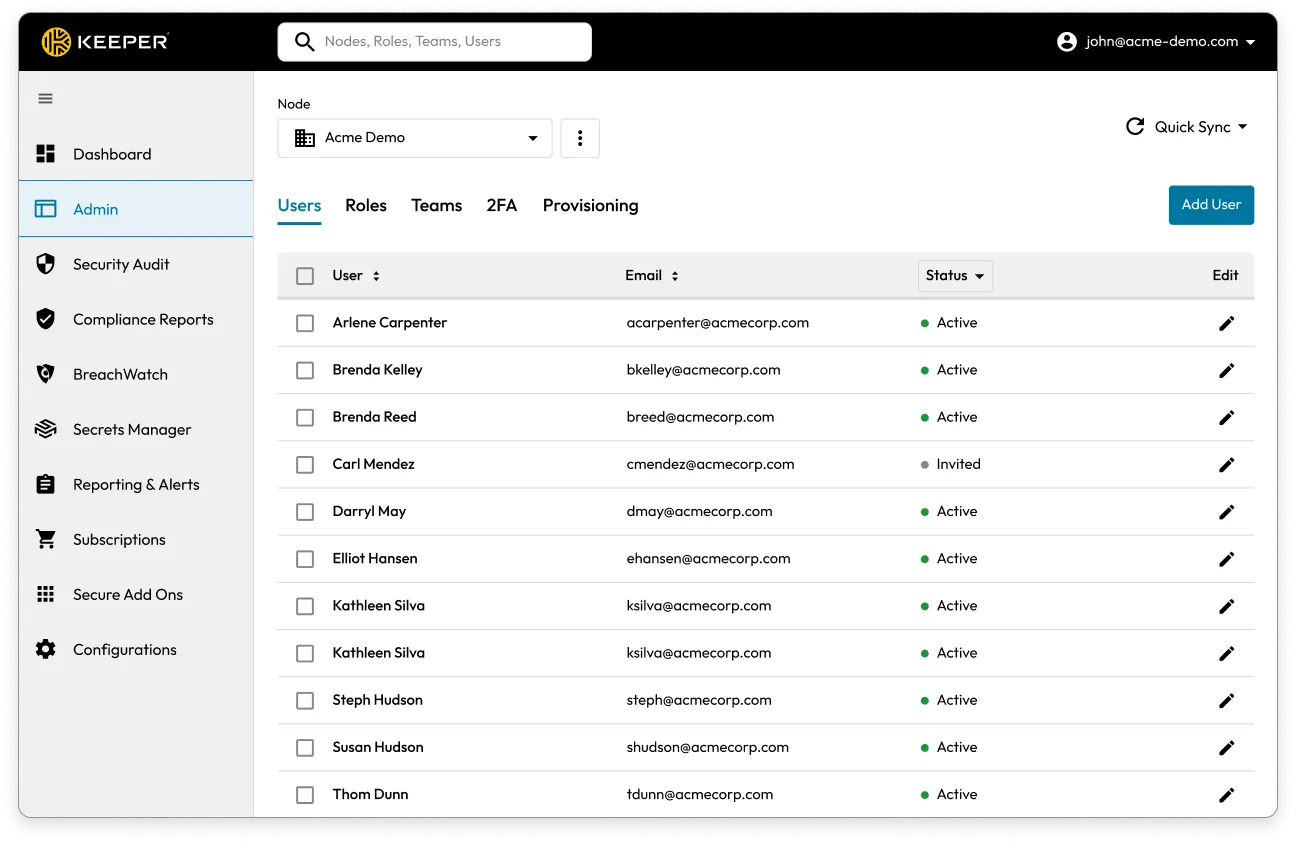
Meeting CMMC's security controls requires a combination of people, processes and technology. By implementing Keeper Security Government Cloud (KSGC), DoD contractors can address coverage on 26 of the 110 controls in CMMC level 2. See the table below for a detailed list of controls covered by KSGC.
The majority of CMMC's security controls are based on NIST 800-171 Revision 2, which was released in 2020. NIST 800-171 Revision 3 is being released in the 1st quarter of 2024 and includes new password security requirements
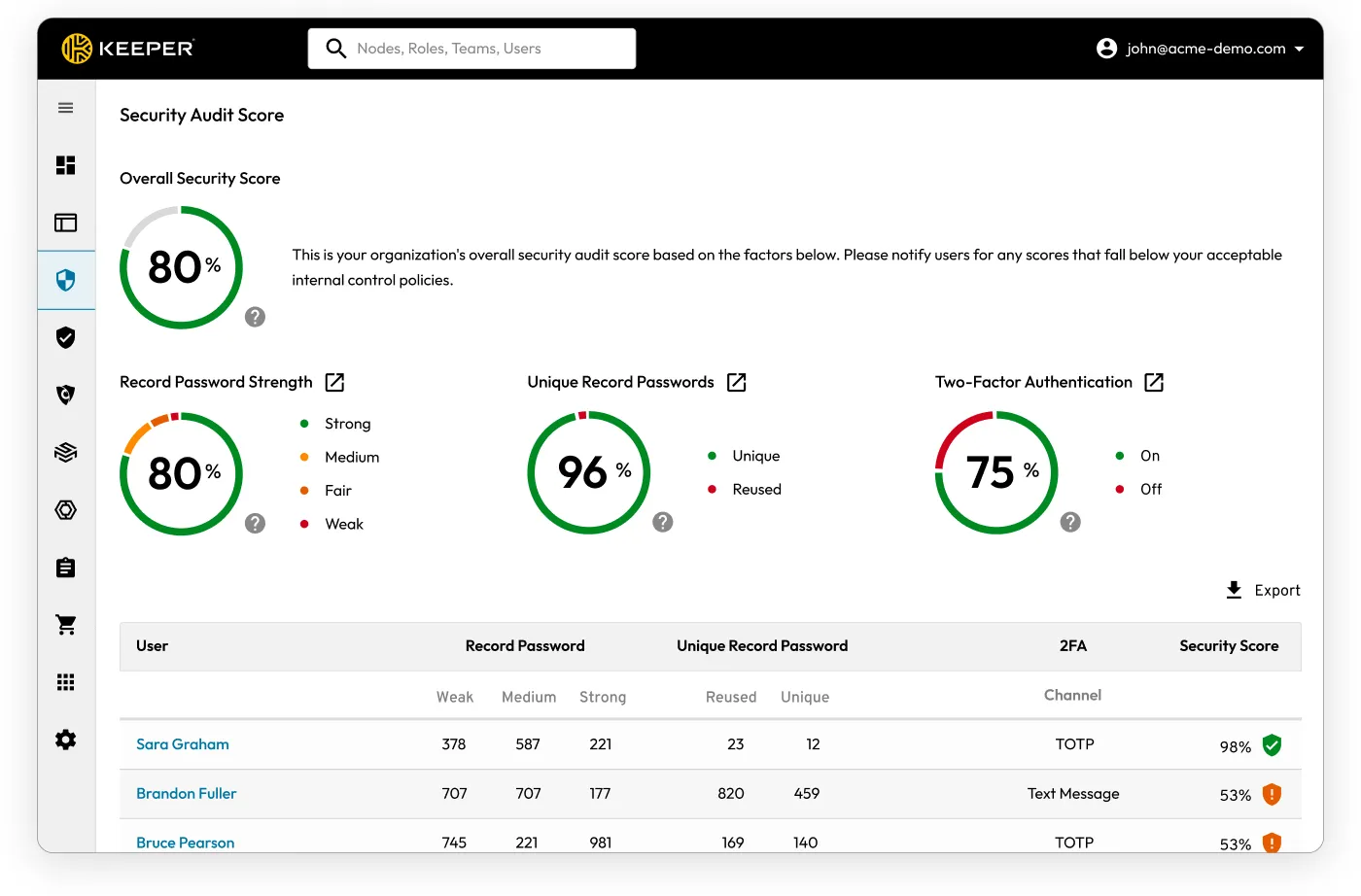
Many DIB IT teams lack visibility into their organisation’s password security posture. KSGC analyses the strength and security of stored passwords across the organisation. KSGC assesses each password against criteria for complexity, uniqueness, and potential exposure on the dark web, providing a comprehensive risk score for individual credentials and the overall password hygiene of the organisation. IT administrators receive actionable insights through detailed reports and dashboards, highlighting weak, reused, or compromised passwords, enabling them to proactively enforce password policies and initiate corrective measures.
KSGC's continuous monitoring and alerting system ensures administrators can quickly respond to potential security vulnerabilities, significantly enhancing the organisation's defense against cyber threats by maintaining strong, secure credentials.

DIB organisations regularly receive and collaborate with the DoD on CUI files. CMMC requires that organisations follow strict security protocols when sharing CUI, such as using encryption and limiting access to only authorised users.
Email is generally not encrypted, making it possible for cyber criminals to intercept emails and attachments in transit. Sending sensitive information over email also risks the information being forwarded, saved or printed without the sender's permission.
Some contractors use Microsoft Encrypted Email, which sends the recipient to a secure login screen to access the email with the files. However, in many cases, internal controls on government machines do not allow this login process to occur, so the agency doesn’t receive the information.
Alternatively, DIB contractors can create an encrypted PDF and then separately send the agency the password for the PDF via a plaintext email. This process is cumbersome, insecure and not user-friendly for employees.
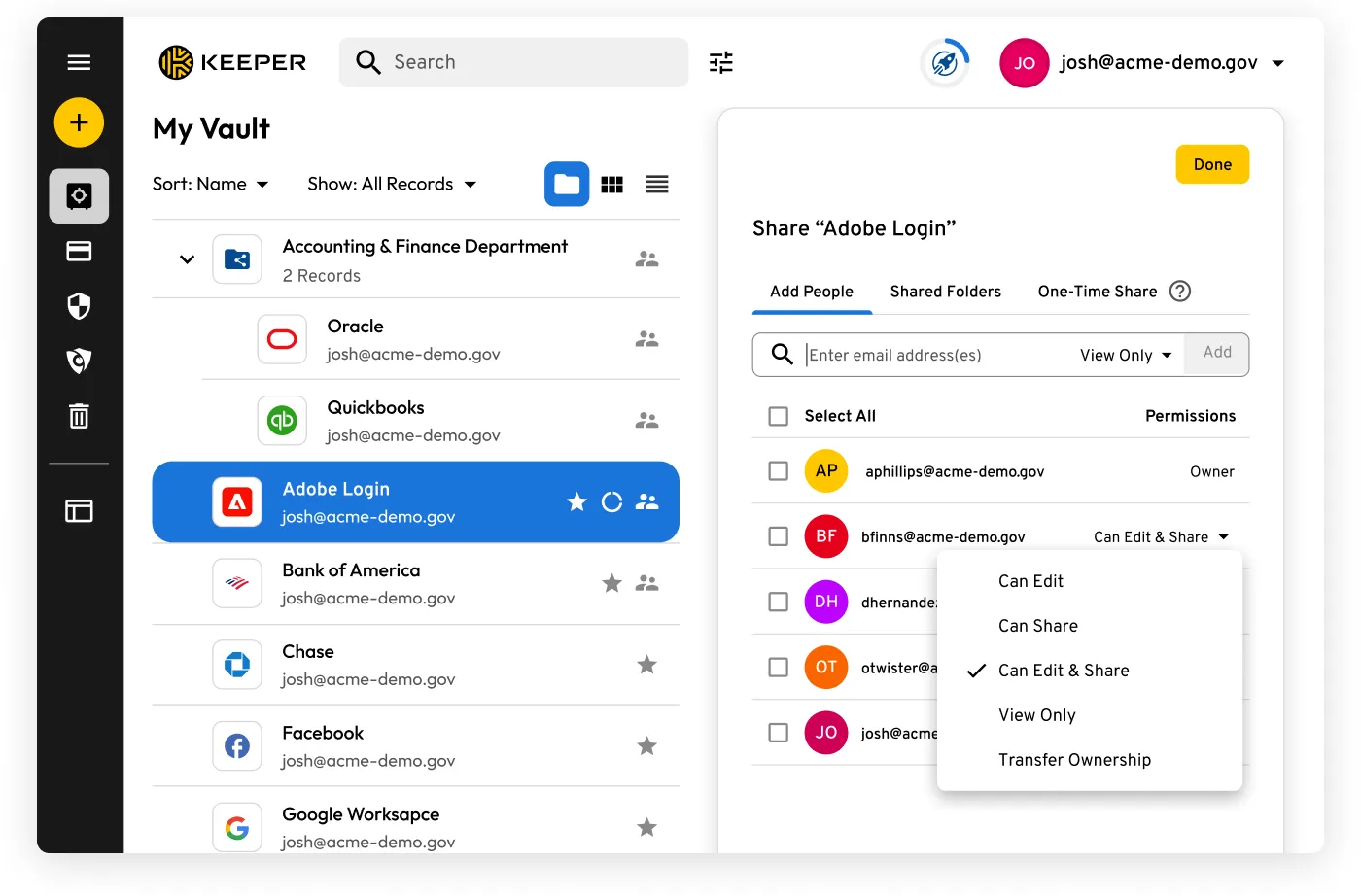
KSGC has built-in FedRAMP Authorised file-sharing capabilities and provides a secure and user-friendly way to share files. Keeper offers secure vault-to-vault sharing and one-time sharing with elliptic curve encryption, meaning cybercriminals cannot intercept passwords or files in transit. Only the intended recipient can access the shared record. With One-Time Share, recipients are not required to log in or be licensed with Keeper to open and download the encrypted file.
Additionally, logs within Keeper show all sending and receiving information for one-time sharing. Real-time security alerts can also be turned on to notify system administrators via text, email or messaging platforms such as Slack or Teams when sharing occurs.
Encrypted file sharing is a must for any organisation that works with the DoD. Keeper allows organisations to store and share their confidential files in an encrypted format for streamlined compliance and auditing.
CMMC will eventually adopt the 3rd revision of NIST 800-171, and defense contractors will need to account for new requirements.
Keeper Security Government Cloud password manager and privileged access manager is FedRAMP Authorised and maintains the Keeper Security zero-trust security framework alongside a zero-knowledge security architecture.
KSGC provides: