What Is Keeper Secrets Manager?
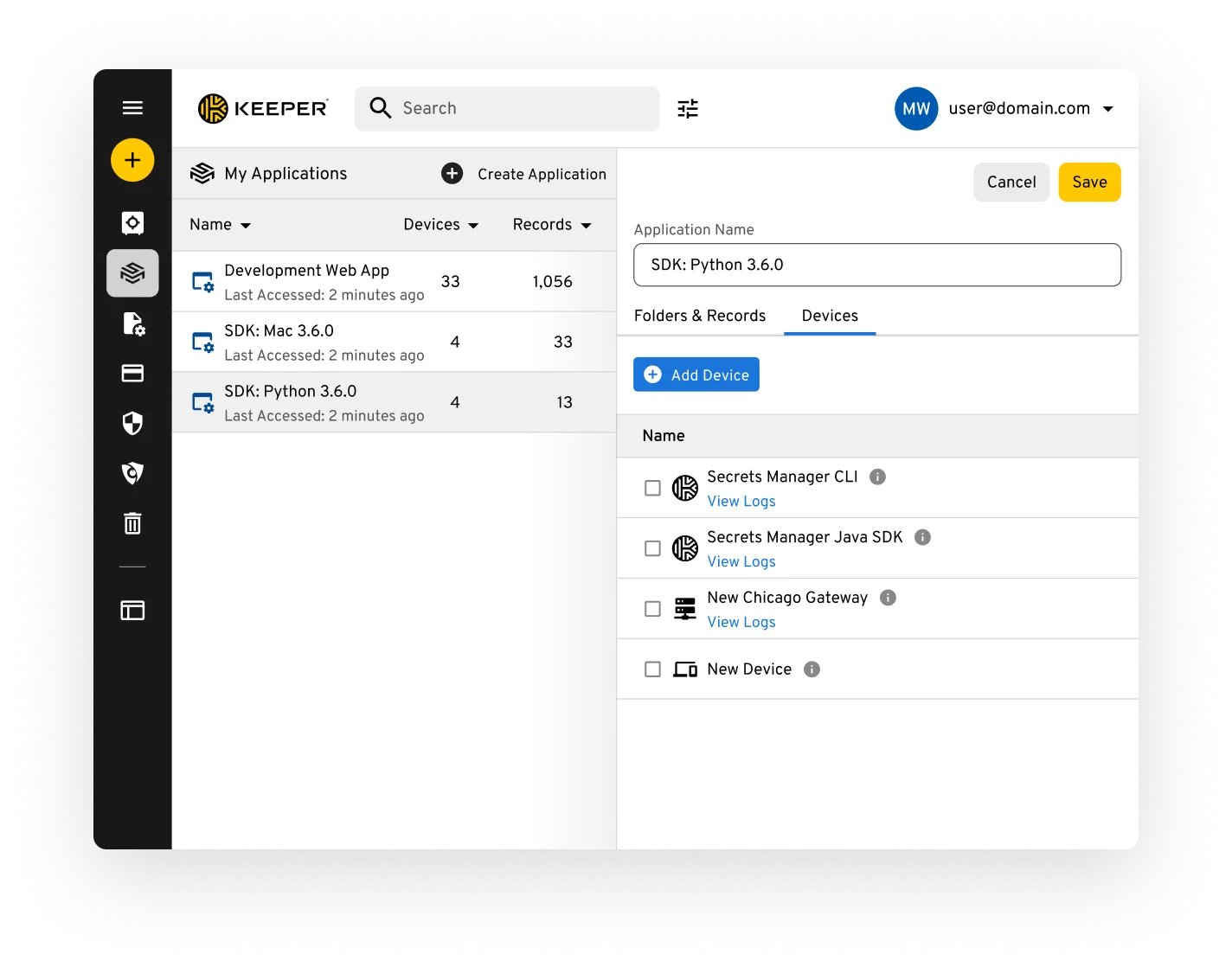
Keeper Secrets Manager (KSM) is a multi-cloud, zero-trust and zero-knowledge platform built for DevOps and technical teams. It is designed to secure infrastructure secrets including access keys, secret credentials, database passwords, API keys, certificates and other privileged credentials – even those stored within other secrets management tools like AWS Secrets Manager.
With Keeper Secrets Manager, all machines, CI/CD pipelines, developer environments and source code pull secrets from a secure and encrypted API endpoint. Keeper Secrets Manager uses several layers of 256-bit AES encryption, and data is always encrypted or decrypted on the user’s device, meaning only authorized users and machines can view and decrypt stored data. Keeper Secrets Manager provides all DevOps team members with a secure vault for managing their secrets, assigning secrets to applications and running reports. Integration into SIEM solutions provides admins with auditable reporting and alerts capabilities.